ConcreteCMS Matrix Chat Client: Project Outline
What It Is
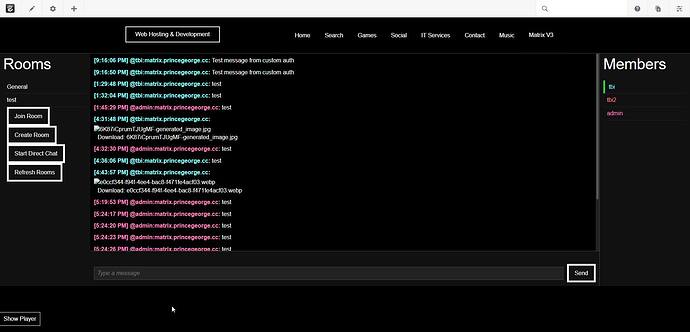
The ConcreteCMS Matrix Chat Client is a Currently a single-page application that connects ConcreteCMS with the Matrix communication protocol. It lets users log in to their Matrix accounts from within ConcreteCMS using JWT authentication. The server-side logic is handled by PHP, while the client-side communication uses JavaScript with the Matrix JS SDK. It’s built to provide a simple, integrated chat experience without leaving the ConcreteCMS platform.
Planned Main Features
- Secure Login: Authenticates users with JWT tokens for a safe and efficient sign-in process.
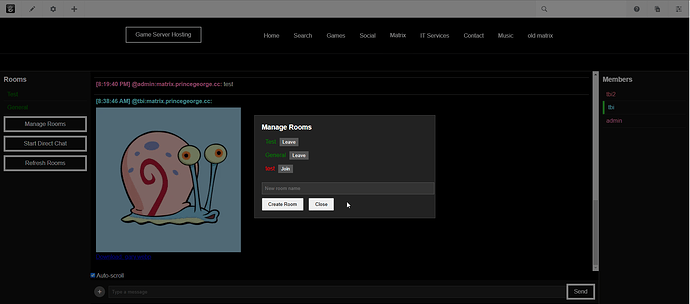
- Real-Time Messaging: Supports sending and receiving text, images, video, and files in a live chat feed.
- Room and Member Tools: Allows users to view and join rooms, check member lists, and start direct chats.
- Typing Indicators: Shows when others are typing to improve real-time interaction.
- Simple Controls: Messages can be sent with a button or the Enter key, and room lists can be refreshed easily.
- Server Federation: Federate multiple ConcreteCMS websites together, allowing a shared social media experience between multiple web properties.
Purpose for ConcreteCMS
This project aims to bring secure, accessible communication to ConcreteCMS users. By using Matrix’s decentralized protocol, it gives users control over their data while offering a practical tool for community discussions, team collaboration, or support channels. It’s being designed to fit seamlessly into ConcreteCMS, enhancing how users connect and interact.
###Current Proof of Concept: