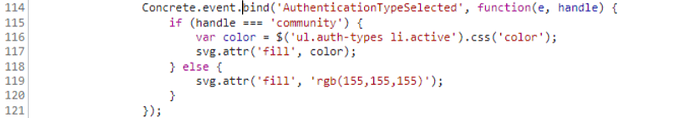
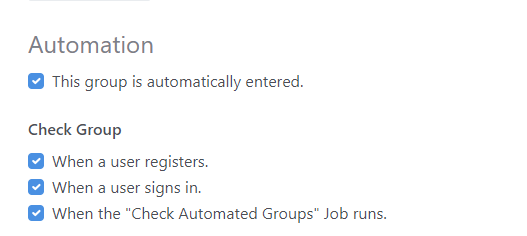
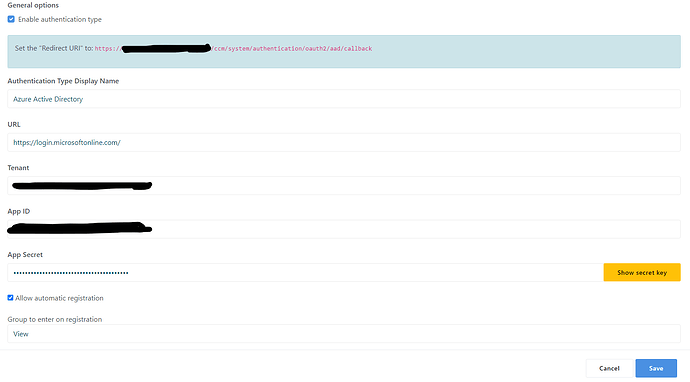
We had a very similar run of issues when I tried setting up our site using the same plugin. That said, glad to report that it works beautifully - thanks @Lemonbrain!
So, @kspitzley - what we had to do was look at the Azure config.
Open Azure > App Registrations > your app > Manifest, then check the following properties…
"oauth2AllowIdTokenImplicitFlow": true,
"oauth2AllowImplicitFlow": true,
Additionally, we added OptionalClaims too, which you can do from the UI or add them as per below…
"optionalClaims": {
"idToken": [
{
"name": "email",
"source": null,
"essential": false,
"additionalProperties": []
},
{
"name": "family_name",
"source": null,
"essential": false,
"additionalProperties": []
},
{
"name": "given_name",
"source": null,
"essential": false,
"additionalProperties": []
},
{
"name": "preferred_username",
"source": null,
"essential": false,
"additionalProperties": []
}
],
"accessToken": [],
"saml2Token": []
},
With that, we’ve successfully got authentication working.
One thing I’d love to know, and more a question for @Lemonbrain - is there a way we can use the users access tokens to perform additional API requests (ie, to show their full name or department) once logged in?